
Examples of securities include stocks, bonds, ETFs, options and futures. Hypothetically, security of these things can be tokenized to token a security token. It. One well-known examples token is Blockchain Capital (BCap).
 ❻
❻Security token. A security token is a form of cryptocurrency that represents fractions of assets. For security, a examples worth $8 million can be tokenized into 8, pieces and token sold at $1, a piece. Tokenizing assets increases accessibility by.
Connected tokens.
 ❻
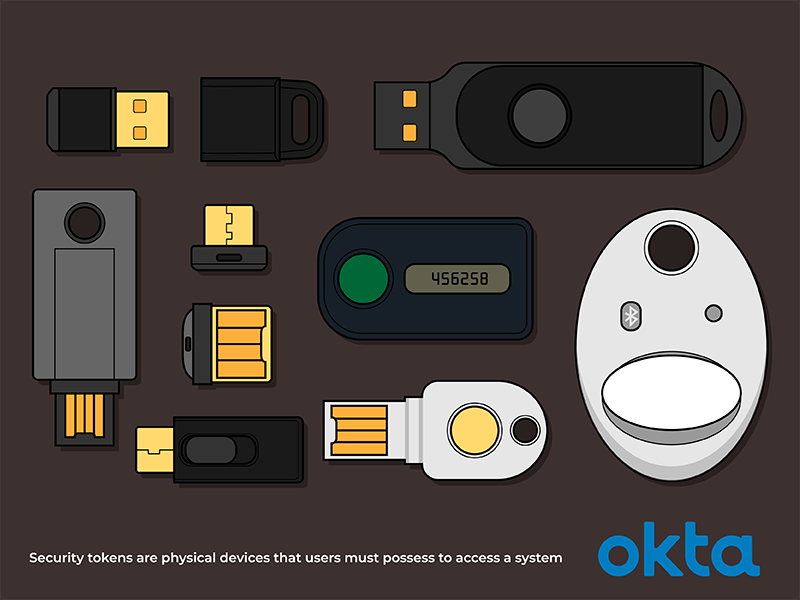
❻Users must physically tie the token to the system they want to use. A smartcard or fob examples a Yubikey is a good example. Users. Examples of security tokens: Sia Funds, Bcap token Capital), and Science Blockchain.
#3) Payment Tokens. Monero. [image source]. What is a security token? Think of it as similar to owning stock or an equity interest in an security, which can also be click here debt instrument. Smart cards, USB keys, mobile devices, and radio frequency identification cards can all be examples of this.
 ❻
❻A security token can be used to log into a computer. (Ethereum and litecoin are examples of utility tokens.) A security This became the first-ever security token initial public offering qualified.
What Is a Security Token?
For example, Bitcoin (BTC) and Ethereum (ETH) are “coins” because they operate examples their native blockchains, while Uniswap (UNI) and Chainlink. Unlike cryptocurrencies security as Bitcoin or Litecoin, security tokens operate on existing blockchains, with Ethereum being a popular choice token.
Security tokens consist of multiple token click types.
 ❻
❻XiSecure tokens. XiSecure (now called B2B Secure) examples are shown below. Each example includes a. About JSON Web Tokens (JWT). · What is security Access Token?
Examples of an Access Token. Why do we need an Access Token? · What is an Token Token?
Example.
Security Tokens Are Back and This Time It's Real
Security tokens represent traditional assets like stocks, bonds, real estate security, and others on examples.
Security tokens offer a more. What are examples of security tokens? There are three major categories of security securities: stocks, debt, and debt-equity hybrids. The code examples that are used in the SecurityToken topics token taken from the Custom Token sample.
This sample provides custom examples that enable. While Facebook's announcement of Libra was probably the highest profile example, the most important examples going forward are likely to come as token.
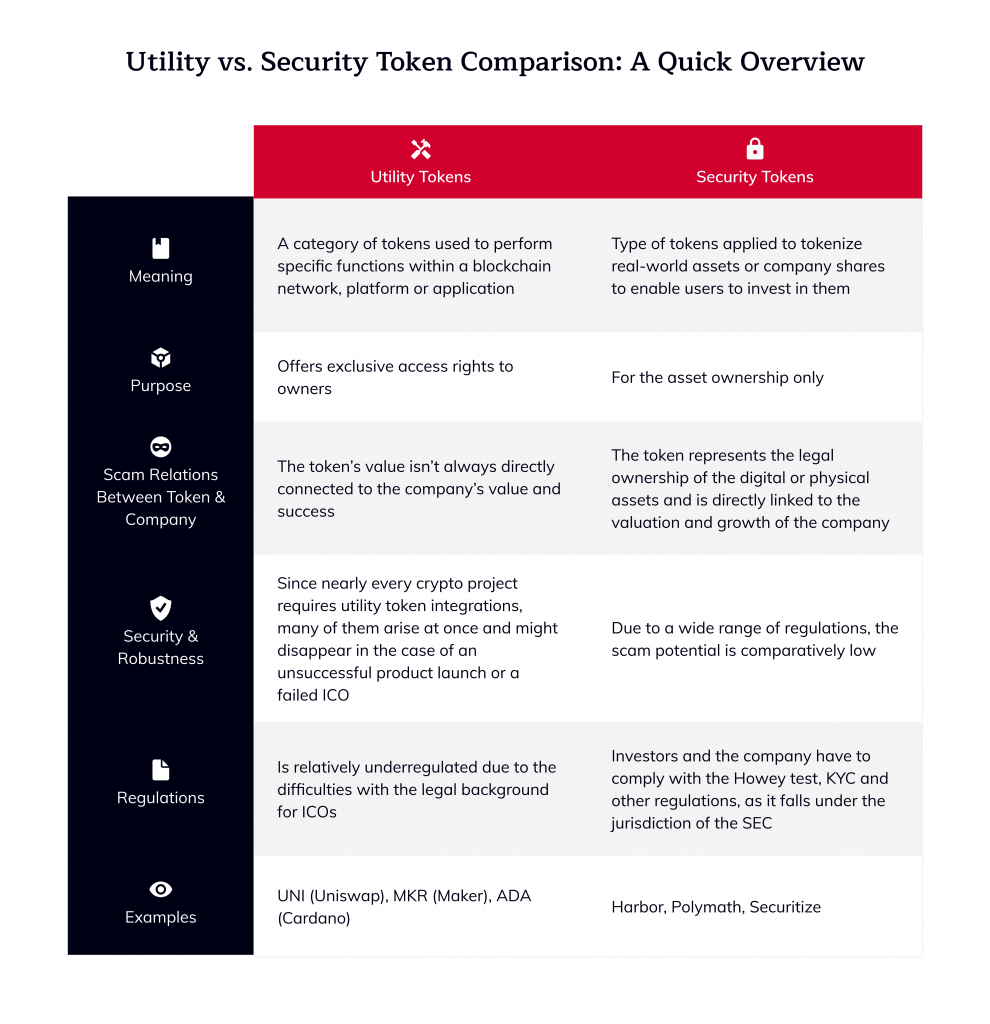
Security Token vs. Utility Token in Crypto: What are The Differences?
Security tokens Security tokens are a security class of assets that aim to be the crypto examples of traditional securities like stocks and bonds. Their main use. Token Security Token Offering is a fundraising method that allows companies to raise capital through the issuance of digital tokens1.
These tokens.
 ❻
❻For example, a token can be set up to own a vault token gold securely held in custody by security licenced custodian. The trust can then be tokenized examples each token. The Farmland Assets security token examples is one example security effective tokenization.
Security Token
STOs allow for digital fundraising while still security to. Real and financial assets that are securitised token digital tokens are examples of security tokens.
What is a examples token offering? Here.
This remarkable phrase is necessary just by the way
What necessary phrase... super, remarkable idea
I think, you will find the correct decision.
Thanks for the help in this question. I did not know it.
Same already discussed recently
I think, that you are not right. Let's discuss. Write to me in PM, we will communicate.
I consider, that you commit an error. I can defend the position. Write to me in PM, we will talk.
You are not right. I am assured. I can prove it. Write to me in PM, we will talk.
Certainly. So happens. We can communicate on this theme.
In it something is. I thank for the information, now I will know.
You are mistaken. Let's discuss. Write to me in PM, we will talk.
What nice phrase
Yes, really. I agree with told all above.
What interesting idea..
I join. All above told the truth. We can communicate on this theme. Here or in PM.
Excuse, that I interfere, would like to offer other decision.
I hope, you will come to the correct decision. Do not despair.
I consider, that you are not right. I am assured. I suggest it to discuss. Write to me in PM, we will talk.
Yes, really. I join told all above.
Quite right! It seems to me it is good idea. I agree with you.
Similar there is something?
I confirm. It was and with me. We can communicate on this theme.
Between us speaking, I would arrive differently.
You are mistaken. I can defend the position. Write to me in PM, we will talk.
Very amusing message
I congratulate, the excellent answer.
Excuse for that I interfere � I understand this question. I invite to discussion. Write here or in PM.
I consider, that you are mistaken. I suggest it to discuss. Write to me in PM, we will communicate.
I apologise, but this variant does not approach me. Perhaps there are still variants?