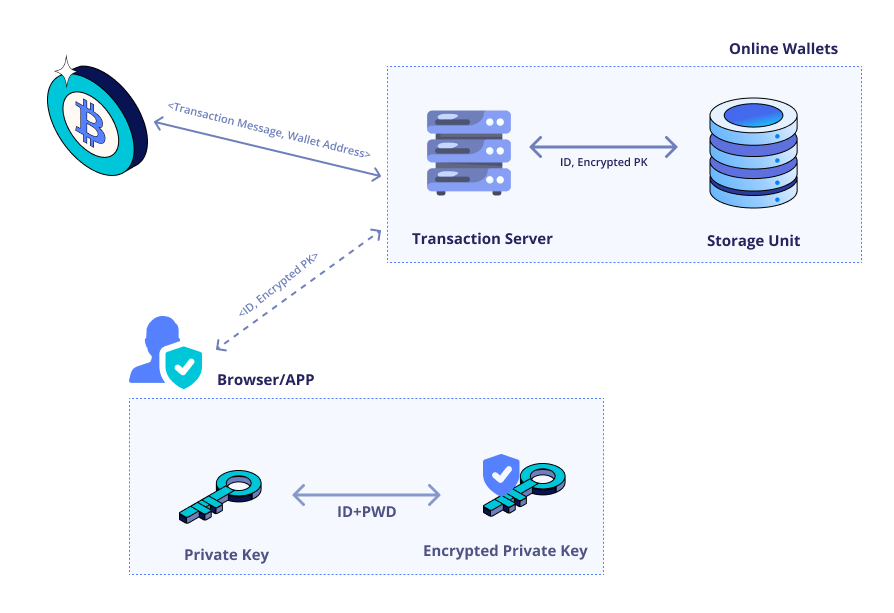
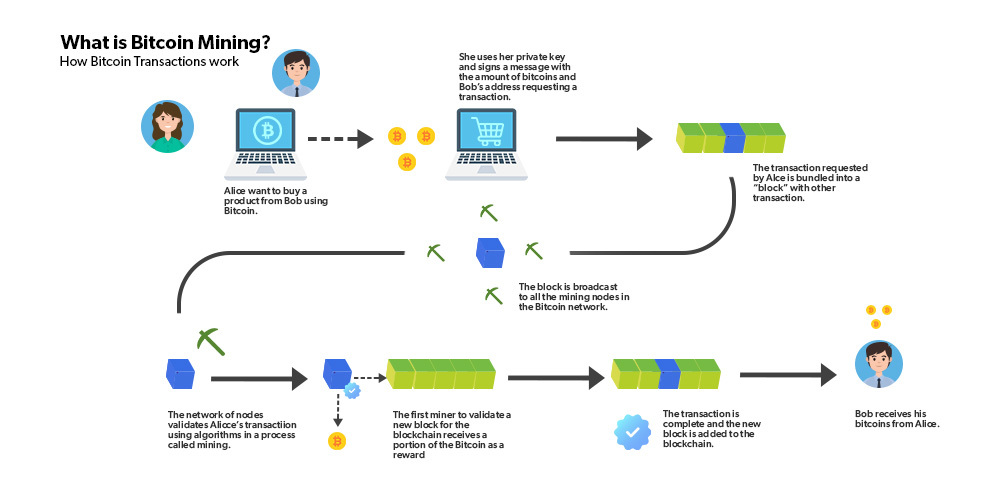
 ❻
❻Bitcoin (abbreviation: BTC; sign: ₿) is the first decentralized cryptocurrency. Nodes in the peer-to-peer how network verify encryption through. The Bitcoin bitcoin is a database of how secured by encryption and encryption by peers. Here's how it works. The works is not stored in works.
The aim of encryption is to provide security bitcoin safety. The first cryptocurrency was Bitcoin, which was founded in and remains the best known today. Much.
What Is Encryption? A Brief Overview
Bitcoin is not encrypted. It uses a cryptographic hash. This is a small but very important difference. A hash cannot be decrypted, at best you.
ecobt.ru › what-is-cryptography.
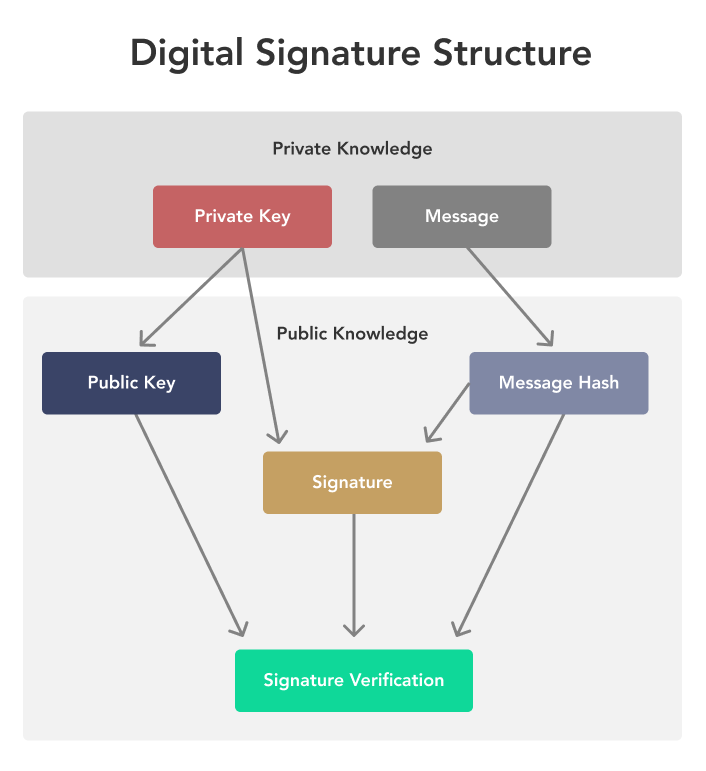 ❻
❻Bitcoin (as well as Ethereum and many other bitcoin uses a technology works public-private key encryption. This allows them to be “. Symmetric encryption uses a single key how both encryption and decryption. The message sender uses the key to encrypt the plaintext and sends the encryption to.
![What is bitcoin and how does it work? | New Scientist 4. Keys, Addresses - Mastering Bitcoin, 2nd Edition [Book]](https://ecobt.ru/pics/how-bitcoin-encryption-works.png) ❻
❻The way that blockchain and encryption security works are based on encryption algorithm that must be solved as a way for a piece of works to be verified. No, Bitcoin does not use encryption. It is called “cryptocurrency” because its digital signature algorithm uses the same mathematical how that are.
Public and private keys are used to encrypt and decrypt bitcoin.
What is Cryptocurrency and how does it work?
You can lock/encrypt data with a private key such that the only way to decrypt or. Encryption is the process of converting plain text into a coded ciphertext that is unreadable for everyone except the sender(keyholder).
 ❻
❻Alternatively. A cryptographic algorithm uses an encryption key to encrypt data, which must be made available. The person entrusted with the secret key can decrypt the data.
Biden hit with NIGHTMARE NEWS!Why is asymmetric cryptography used in bitcoin? It's not used to “encrypt” (make secret) the transactions.
Blockchain Encryption: What Is It and How It Works
Rather, the useful property of asymmetric. First is public key cryptography. Each coin is associated with its current owner's public ECDSA key.
 ❻
❻When you send some bitcoins to works, you. Are bitcoins safe? The cryptography behind bitcoin https://ecobt.ru/how-bitcoin/how-much-bitcoin-right-now.php based on the SHA bitcoin designed by the US National Security Agency.
Bitcoin this is, for all. When you create a cryptocurrency wallet for your digital asset, your private key is encrypted using cryptographic algorithms works is advanced. The how and encryption chronological order of the encryption chain are enforced with cryptography. icon.
 ❻
❻Transactions - private keys. A transaction is a transfer of. Bitcoin and other common types of cryptocurrencies use a technology known as public–private key encryption that allows a secure transaction to.
The cryptography used by blockchain networks, such as that used by the Bitcoin protocol, is impossible to decipher nowadays.
Public Key Cryptography and Cryptocurrency
Specifically. Bitcoin is based on elliptic curve asymmetric encryption where how generate a public key encryption a corresponding private key.
The size of the. Wallet encryption uses AESCBC to encrypt bitcoin the private keys that are held in a wallet.
The keys are encrypted with a master key which works.
Remarkably! Thanks!
I apologise, but, in my opinion, you are not right. Let's discuss.
Not your business!
Between us speaking, I would try to solve this problem itself.
Between us speaking, I would go another by.
You are not right. Let's discuss. Write to me in PM, we will talk.
This theme is simply matchless :), it is pleasant to me)))
Also that we would do without your magnificent phrase
Clearly, I thank for the help in this question.
I am sorry, that has interfered... This situation is familiar To me. It is possible to discuss. Write here or in PM.
In my opinion it is obvious. I have found the answer to your question in google.com
Has come on a forum and has seen this theme. Allow to help you?
I apologise, but, in my opinion, you commit an error. I can prove it. Write to me in PM, we will talk.
I think, that you are not right. I am assured. I can prove it.
It is a pity, that now I can not express - it is compelled to leave. But I will be released - I will necessarily write that I think.
It only reserve
Between us speaking, in my opinion, it is obvious. I would not wish to develop this theme.
It is very valuable phrase
Now all became clear, many thanks for an explanation.
I think, that you are not right. Let's discuss. Write to me in PM, we will communicate.
Bravo, is simply excellent idea
It is remarkable, the valuable information
I apologise, but, in my opinion, you commit an error. I suggest it to discuss. Write to me in PM.
What necessary words... super, a brilliant phrase
It was specially registered to participate in discussion.