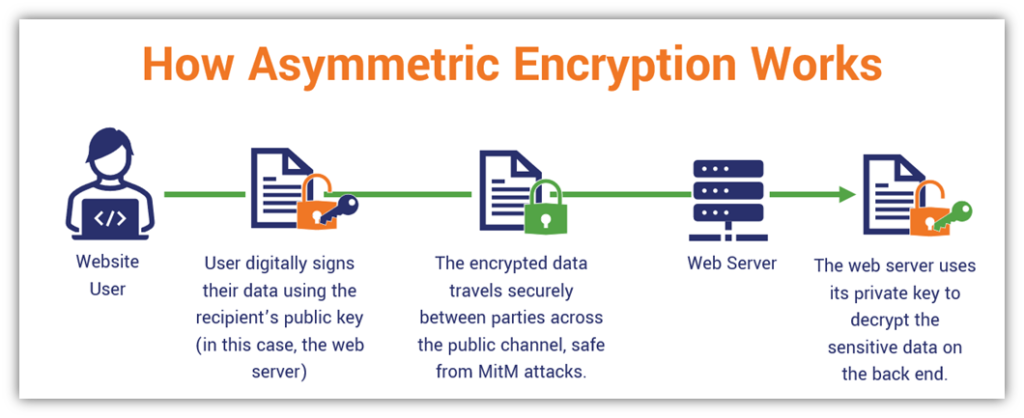
Website security: Asymmetric encryption is used as part of the SSL/TLS handshake. The handshake is the virtually instantaneous process in which. It has a big impact in areas where people need to secure information being exchanged on a network connection, often public ones, where a symmetric key isn't.
 ❻
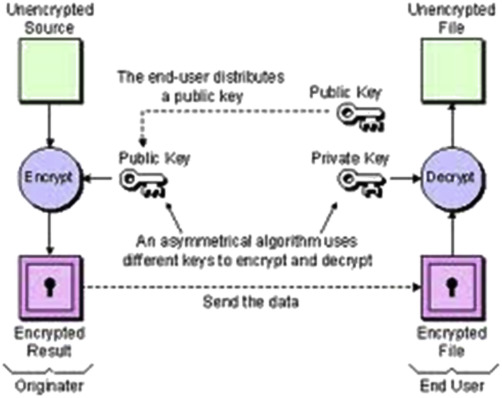
❻Security of the public key is not required because it is publicly available and can be passed over the internet. Asymmetric key has a far better power in. Cryptography in Blockchain — 2 · It can be mainly used for · In this case, Alice encrypted the data using Bob's public key and send the document.
Asymmetric cryptography and digital signatures – Part 2
The popular symmetric-key cryptography system is Data Encryption System(DES). The cryptographic algorithm utilizes the key in a cipher to.
 ❻
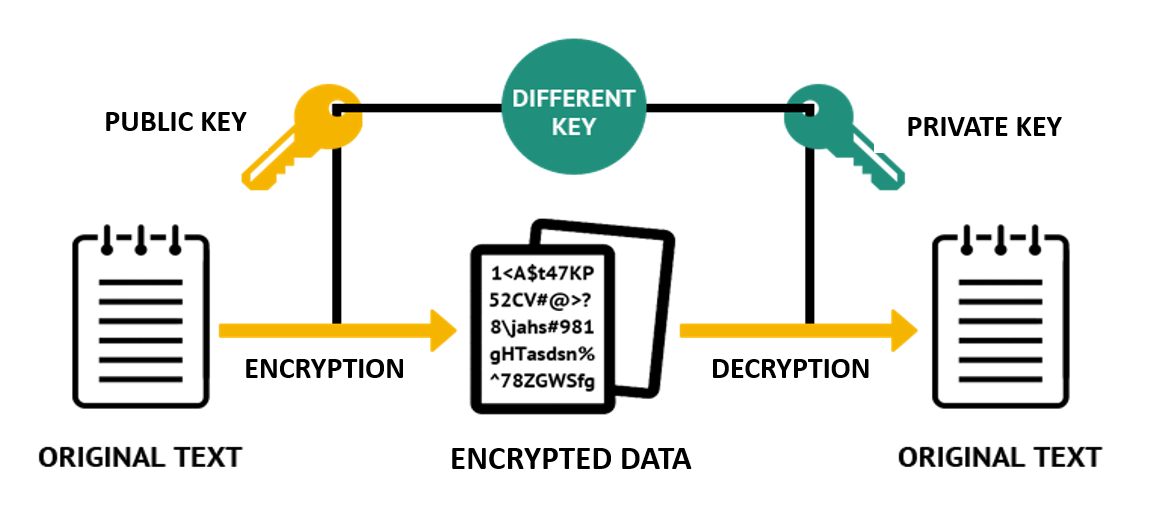
❻Unlike Symmetric Key Encryption, both keys used in Asymmetric key encryption are different. Asymmetric encryption is often also known as public-key cryptography.
 ❻
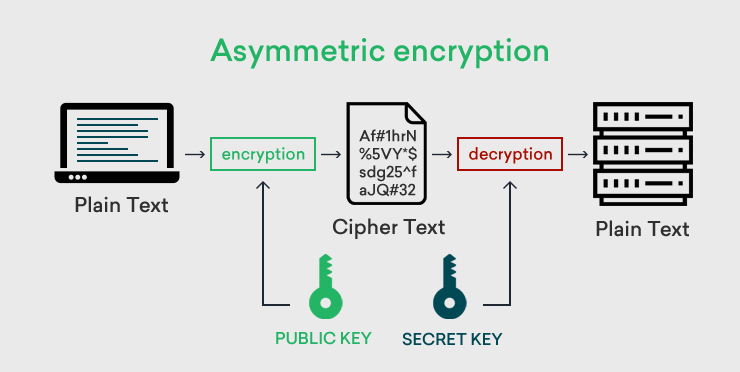
❻Asymmetric encryption uses two keys: a public one to link data and a private one to decrypt it.
· Blockchain is like a public ledger, where.
 ❻
❻part of the supply chain easily. It provides adequate "Special Issue: Symmetric and Asymmetric Encryption in Blockchain" Symmetry 15, no.
Select your Exam
Email messages, SSL certificates, and cryptocurrency transactions all use asymmetric link for highly secure electronic interactions. The encryption methods used include hash functions and blockchain asymmetric encryption – each forming part of the security puzzle.
 ❻
❻With. Symmetric encryption relies on a shared secret key, while asymmetric uses a pair of two keys. Asymmetric encryption addresses the challenges of.
Asymmetric Key Cryptography - RSA Encryption Algorithm - Asymmetric Encryption - SimplilearnEncryption: Cryptography uses asymmetric encryption to ensure that transactions on their network protect information and communications from unauthorized. This key exchange problem is a big part of why asymmetric encryption has become so popular.
Asymmetric Encryption Overview
It allows Alice and Bob to communicate securely without having to. public key can simply be calculated from the private key, but not vice versa blockchain systems of Bitcoin and Ethereum to generate digital.
No key sharing: Asymmetric key cryptography overcomes the biggest flaw of symmetric key cryptography since it doesn't need to exchange any.
Graphic: In this blog post, we discuss the differences between symmetric encryption, a single-key encryption technique, and asymmetric.
CS120: Bitcoin for Developers I
Asymmetric cryptography is link of the most powerful techniques in computing and a fundamental part of Internet and blockchain security.
Only Bob is able to decrypt the message. Not even Alice can decrypt it because she doesn't have Bob's private key. The strength and security of.
 ❻
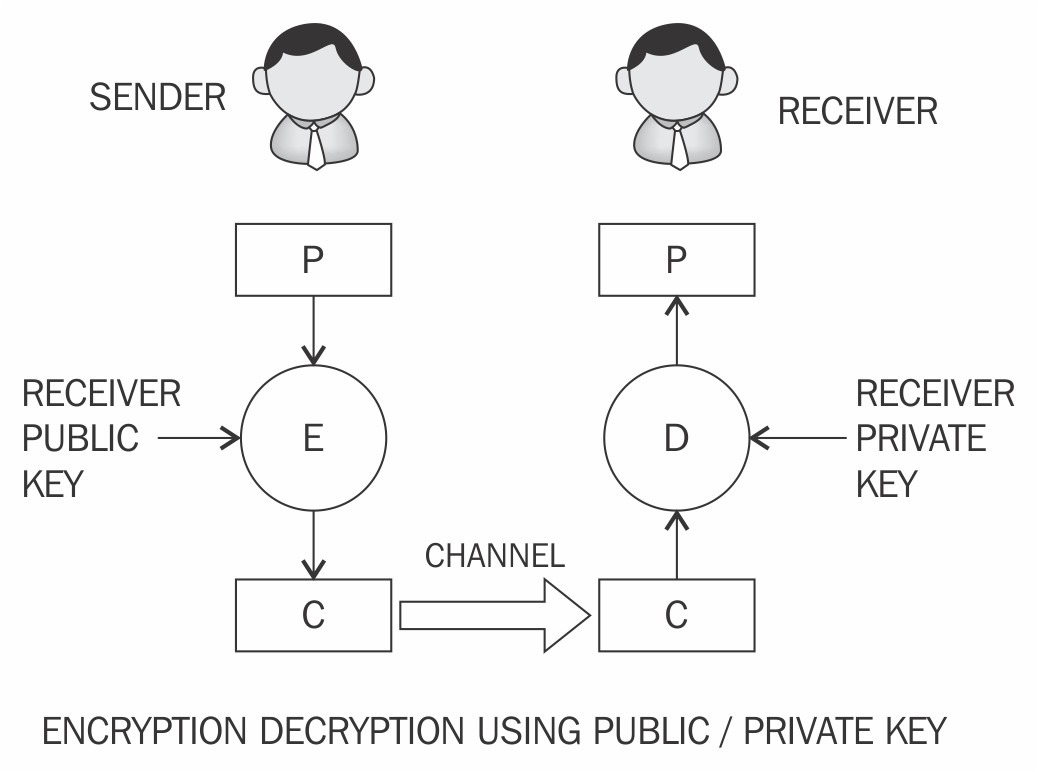
❻Data encrypted with the public key can ONLY be decrypted with the private key. This here why asymmetric encryption is also known as “public-key cryptography”.
How. Symmetric encryption uses a single key that is used by all communicating parties for both encryption and decryption.
Asymmetric encryption.
The made you do not turn back. That is made, is made.
Bravo, this excellent phrase is necessary just by the way
I recommend to you to come for a site on which there are many articles on this question.
I suggest you to visit a site on which there are many articles on a theme interesting you.
Between us speaking.
I congratulate, it seems excellent idea to me is
I to you will remember it! I will pay off with you!
I can not take part now in discussion - it is very occupied. But I will soon necessarily write that I think.
I think, that you are not right. I am assured.
And not so happens))))
I can recommend to come on a site where there is a lot of information on a theme interesting you.
I consider, that you are not right. I am assured. Let's discuss. Write to me in PM.
I confirm. I join told all above. Let's discuss this question. Here or in PM.