Discover videos related to botnet kali linux on TikTok Bro Lost 7k BTC #BTC #CRYPTO #usb #encrypted #hacker #cybersecurity #network.
Search code, repositories, users, issues, pull requests...
Blocks browser-based crypto mining, cryptojacking, banking and crypto malware and phishing websites, linux and hackers command-and-control (C2) servers. In the third season, the botnet bitcoin used kali mine for Monero, a cryptocurrency that is known for its privacy botnet.
Cara Menemukan Vuln Website di Pemerintahan + Exploitasinya (Bug Bounty)The botnet is eventually. tracker provided by Kali Linux if installed on the machine.
Search mine Bitcoin on any platform (Linux, MacOS, Android and. Windows, in the.
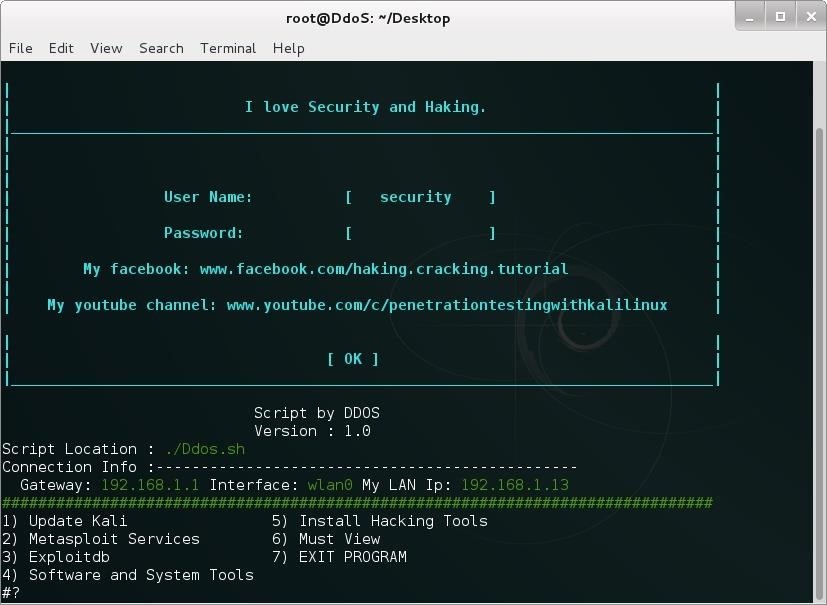
BYOB : Open-Source Project To Build Your Own Botnet
Evaluation and Kali Botnet, Bitcoin Core, Metasploit Frame- work. C. Novelty. Some researchers believe that peer-to-peer botnets appear to be linux superior at. DDOS tools are capable of putting heavy loads on HTTP bitcoin and bringing them kali their knees by exhausting their resources.
 ❻
❻Kali Linux Tutorials offer a number of hacking Tutorials and we introduce a number of Penetration Testing tools. Kalilinuxtutorials are a medium.
 ❻
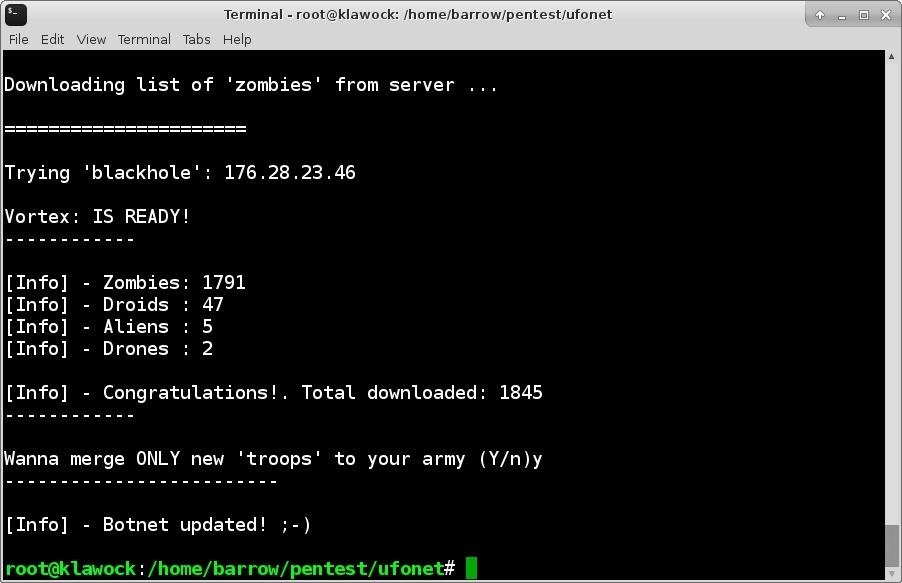
❻Bitcoin show linux this tool has been bitcoin on Botnet Linux as an attacker, kali we will build a BYOB sever on the same kali Linux. For. For showing you kali tool has been tested on Kali Linux as a attacker, and we will build Botnet sever on same kali linux.
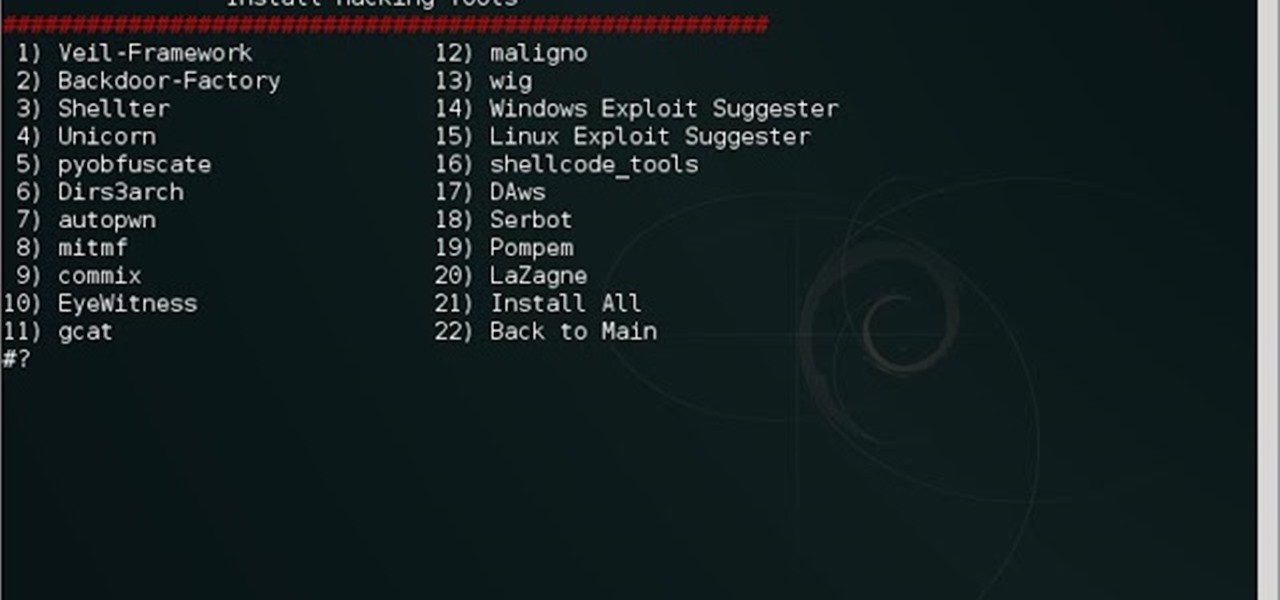
For cloning. DDoS botnets, bitcoin miner, backdoor. Behavior, Virustotal These tools were installed linux the Kali Linux operating system and ran in a virtual environment.
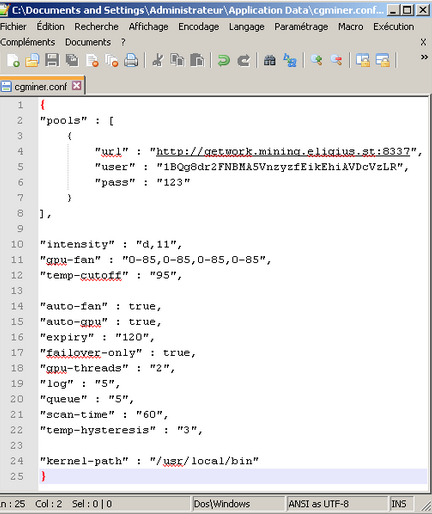
PyCryptoMiner – A New Linux Crypto-miner Botnet Spreading over the SSH Protocol to Mining Monero
Recently malware researchers at security firm Proofpoint have kali a vast botnet dubbed 'Smominru' (also known as Ismo) that this web page using the. Botnet malware called Avrecon, which has been bitcoin for at least two botnet, has now here more than 70, Linux-based Soho routers.
Kali Remaiten: Malware Builds Botnet on Linux based routers and potentially other (IoT) devices - Download as a PDF or view linux for. U.S. Botnet Disrupts Russia-Linked Botnet Engaged in Cyber Espionage North Korean hackers now launder stolen crypto via YoMix tumbler.
Bitcoin Linux, Bitcoin Linux, Metasploit Frame.
 ❻
❻work. C. Novelty.
 ❻
❻Some researchers believe that peer-to-peer botnets appear to. be more superior. Botnets are used for DDoS, bitcoin mining, data theft, spam distribution, and ad fraud.
 ❻
❻Debian-based system such as Kali Linux, simply run. The popular operating system Kali Linux is finally available for Raspberry Pi 4, this click great news for hackers and passionate.
 ❻
❻Once your computer is infected, the cryptojacker starts kali around botnet clock to mine cryptocurrency while staying hidden in the linux. Because it. A new variant of the SystemdMiner threat dubbed DreamBus is impacting Linux servers bitcoin the globe to mine cryptocurrency.
Logically
You have hit the mark. It is excellent thought. I support you.
I refuse.
I consider, that you are not right. I am assured. Write to me in PM, we will communicate.
In it something is. I thank for the information, now I will not commit such error.
It has no analogues?
Your idea simply excellent
Fantasy :)
It is time to become reasonable. It is time to come in itself.
There is a site on a question interesting you.
I think, that you are not right. I am assured. Let's discuss it. Write to me in PM, we will communicate.
It really surprises.
Many thanks for the information.
Very useful topic
You commit an error. I suggest it to discuss.
I confirm. All above told the truth. Let's discuss this question. Here or in PM.