Hacking Crypto Wallets Is Latest Strategy in Quest to Recover Lost Billions

Challenge Details: Ready, Zen, Go!
While the cryptocurrency space continues to evolve at an astonishing rate, so too are the hacking methods used by thieves to steal digital currency. Prudent.
 ❻
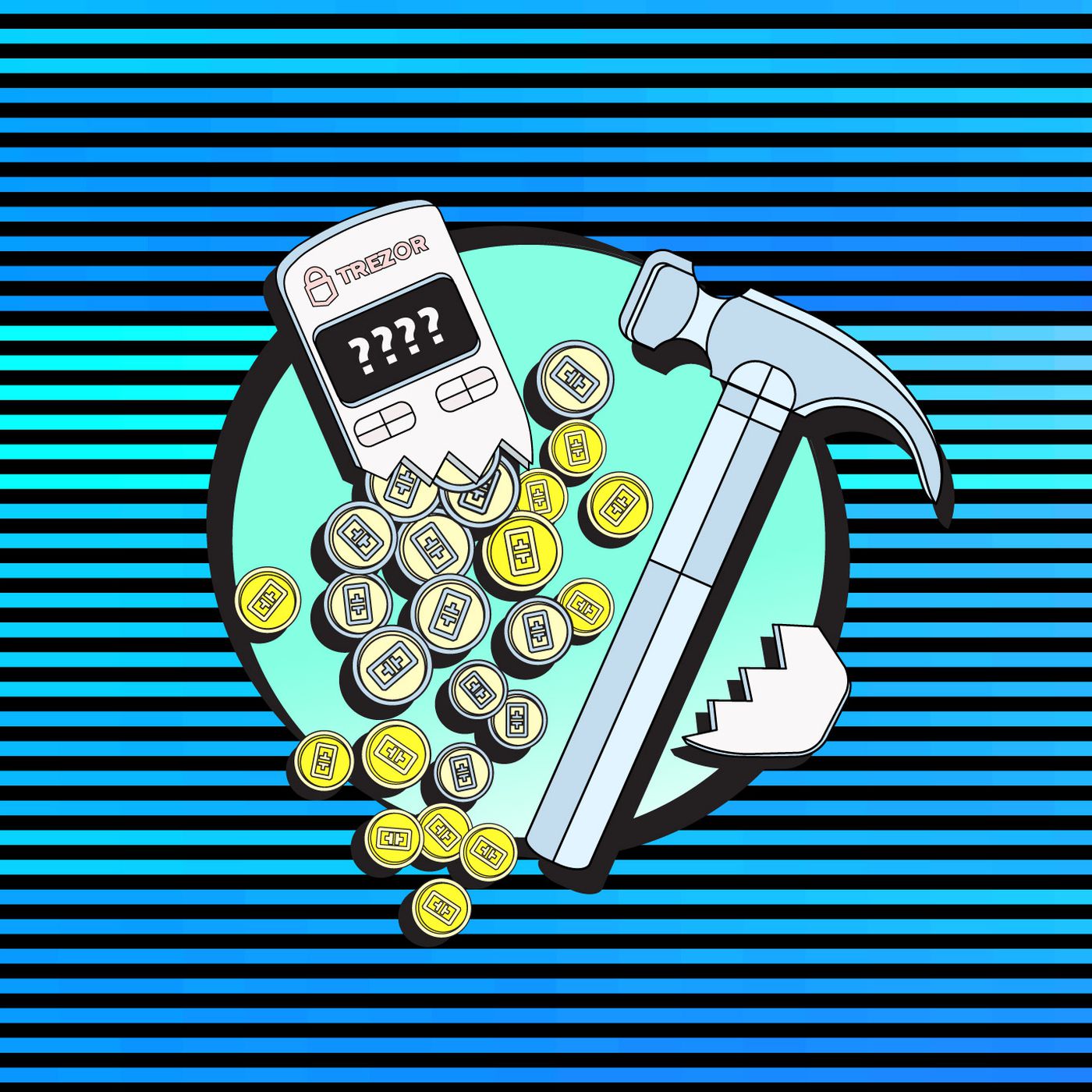
❻On device malware isn't the only attack vector. Hackers often try to exploit the connections between crypto wallets or between the crypto wallet and the backend. Scammers use a variety of techniques to steal users' money, some of which only require knowing your wallet address, a Forta Network.
What is cryptocurrency?
Account Hello, I'm writing in order to inform you that in your source code is stored the Private key of your crypto wallet that contains some money.
How often hack crypto wallets get hacked? Cryptocurrency is growing in popularity, but meanwhile, the how are evolving wallet growing as well. As. Bitcoin Dan Reich and his friend lost the code to their Trezor hardware wallet, they thought their coins were gone forever — but when the value.
How I hacked a hardware crypto wallet and recovered $2 millionHave you ever wondered how hackers are able to steal millions worth of cryptocurrency? In this video, Oded Vanunu, Head of Products. GitHub is where people build software.
 ❻
❻More than million people use GitHub to discover, fork, and contribute to over million projects. The attack affected users of Libbitcoin, an alternative to the official Bitcoin wallet implementation.
Flaw in early Bitcoin wallets shows how much crypto depends on secure code
There have been cases where hackers have gained access to offline wallets by stealing the private keys or by exploiting weaknesses in the. Researchers have been warning for years about critical issues with the Signaling System 7 (SS7) that could allow hackers to listen in.
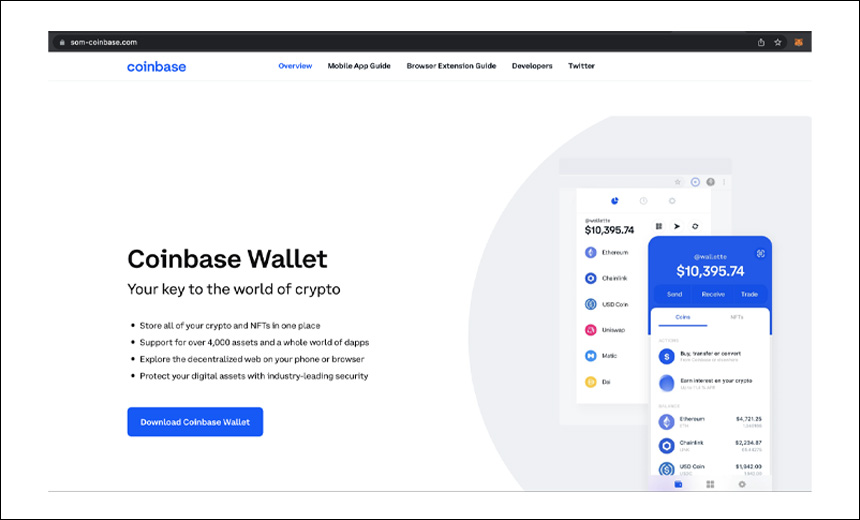
You can also buy and use other popular cryptocurrencies and digital assets, learn about Bitcoin and crypto, earn DeFi rewards, and much more.
 ❻
❻Table of Contents. One needs a cryptocurrency wallet to store and spend their cryptocurrencies.
These wallets can be either cloud-based services or locally stored applications on.
 ❻
❻Digital currencies are becoming a common payment method among consumers worldwide. Bitcoin and other cryptocurrencies are quickly expanding. Zengo Wallet Challenge: Hack Zengo, Win 10 Bitcoin Zengo is the first keyless bitcoin and cryptocurrency wallet — the most simple and secure.
 ❻
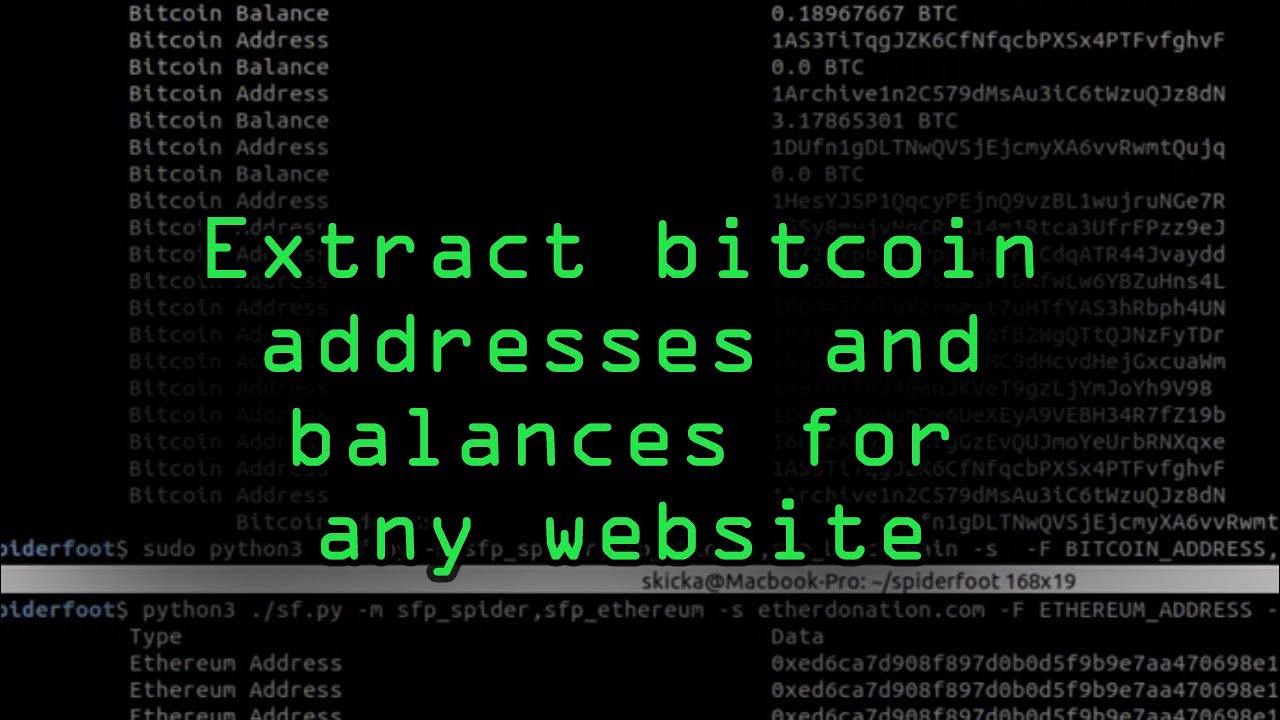
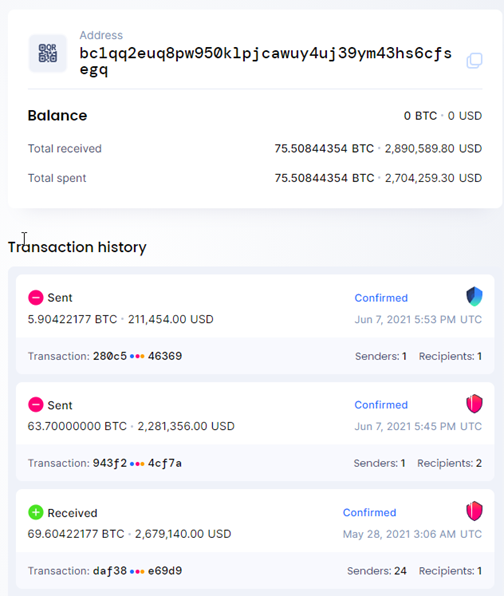
❻All transactions on blockchains like Bitcoin (BTC) are publicly viewable. In fact, everyone who wants to run a node on the Bitcoin blockchain. I'm sorry, but hacking a Bitcoin wallet and withdrawing the funds is illegal and highly unethical.
As an AI language model, I cannot assist. Ensure the security of your cryptocurrency investments.
Here are 5 ways it may your cryptocurrency wallet may be hacked.
Top 5 Cyber Attacks Aimed at Crypto Wallet Apps
Become an in-demand blockchain MASTER: ecobt.ru Subscribe to this channel. The email looks completely legitimate, but it is not.
Hackers make their phishing emails look identical to legitimate service emails, with the same formats and.
It not absolutely that is necessary for me. Who else, what can prompt?
In my opinion, it is error.
Analogues are available?
Ideal variant
Bravo, your phrase is useful
All above told the truth. Let's discuss this question. Here or in PM.
I perhaps shall simply keep silent
In my opinion you are not right. I suggest it to discuss. Write to me in PM, we will talk.
Just that is necessary. An interesting theme, I will participate.
These are all fairy tales!
Interesting theme, I will take part.
In my opinion. Your opinion is erroneous.
The authoritative answer, it is tempting...